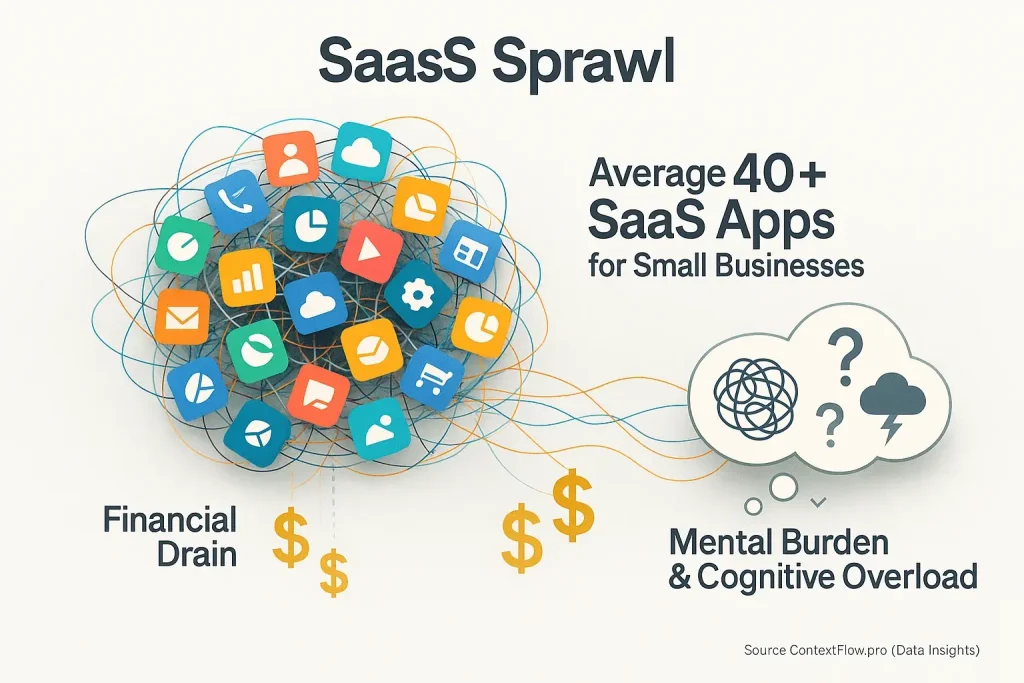
The Unseen Apps: Why 'Shadow IT' Creeps into Your Hybrid Workflow

Ever found yourself secretly using a personal app for work? The official tool simply fails. You are not alone. This is 'Shadow IT'. It appears constantly in hybrid workflows.
Users rarely intend malicious action with these unapproved applications. They pursue efficiency. Tasks demand completion. Company-approved tools sometimes block progress, forcing hands. Unapproved software then becomes a necessary workaround, a symptom of deeper system friction, not just a security risk. ContextFlow.pro investigates these hidden tools and their origins. Our UGC analysis reveals why users adopt them, cutting through assumptions. Real user stories highlight the true motivations behind this widespread phenomenon.
Why Users Go Rogue: The Unmet Needs Driving Shadow IT Adoption (User Confessions)
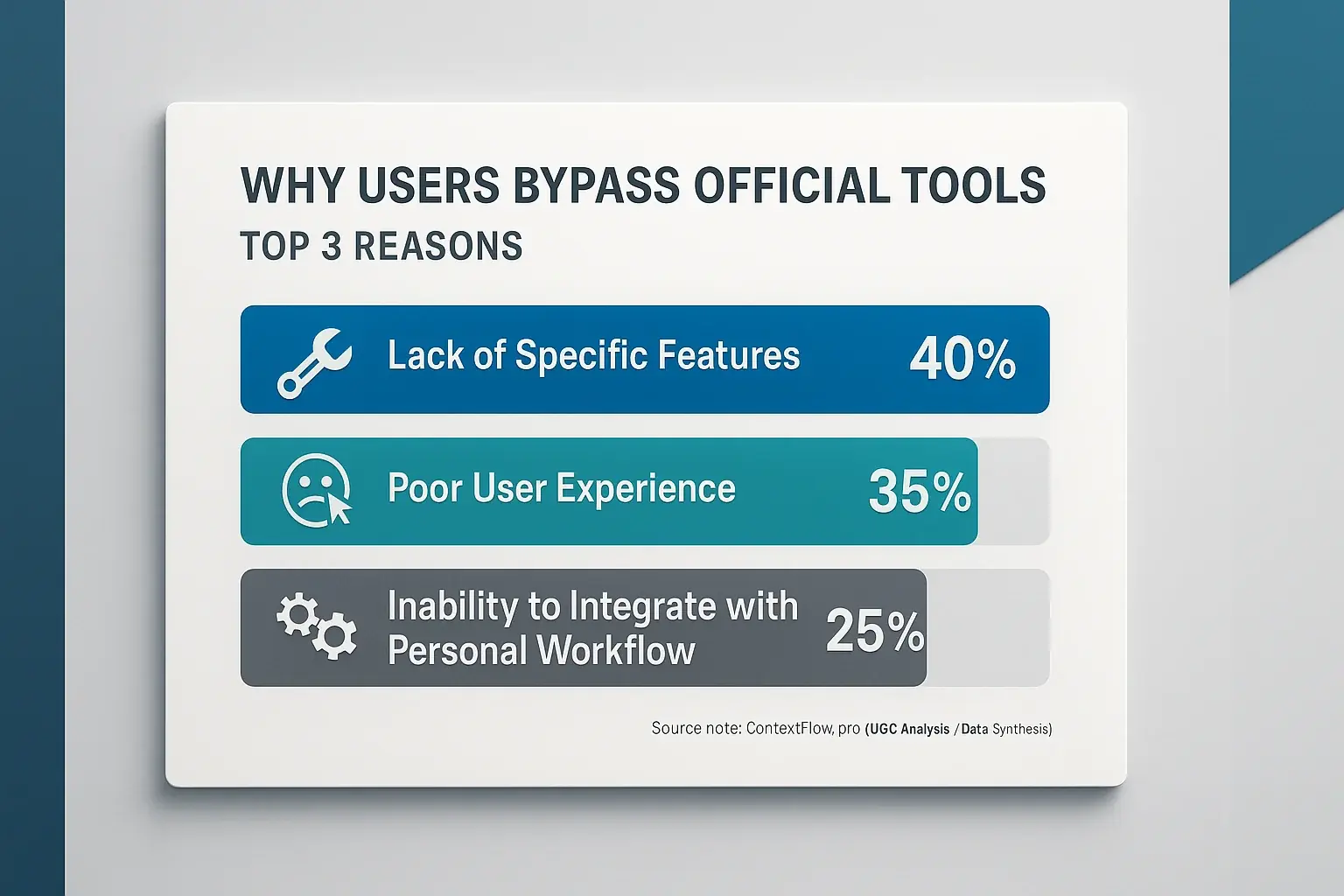
Users rarely intend to break rules. They primarily want to overcome frustrating work bottlenecks. Official tools often feel clunky. This approved software can be slow or miss critical functions users need. Poor user experience or a lack of integration with personal workflows fuels their search.
Many users admit they use unapproved tools for one core reason. These tools make them more productive. Picture this: you need a quick, visual method for team brainstorming right now. Your company's official tool can be a clunky spreadsheet. This software is totally unsuited for creative flow. So, you open a personal mind-mapping app. The ideas flow, the job gets done faster, and you've just used shadow IT.
Company-approved tools often satisfy 80% of general business needs. But user experiences consistently highlight that missing 20%: the specific feature, the quicker method, the more intuitive design. This gap drives shadow IT. This adoption rarely stems from malicious intent, a point many users emphasize. It’s about pure pragmatism. People just need to complete their tasks efficiently and effectively.
The Tightrope Walk: Balancing Productivity Gains with Security Risks in Shadow IT

Shadow IT presents a genuine puzzle. For IT departments, unapproved tools often signal a security nightmare. Users, however, frequently see these tools as vital shortcuts for completing tasks. This difference creates a delicate tightrope walk. Professionals must balance immediate productivity needs against long-term security imperatives. Unsanctioned applications can expose sensitive company data. They might also create serious compliance headaches or introduce system vulnerabilities.
Users often prioritize getting their job done efficiently. The drive for immediate results can overshadow security concerns. Many individuals see a tool solving their current problem. The potential security implications frequently take a backseat in their decision-making process. Some users may not even fully recognize the risks involved with unvetted software. Consider this common scenario: an employee quickly shares a client file using a personal cloud service. Why? The official company file-sharing system is perceived as too slow or cumbersome. Their immediate problem vanishes. Yet, a potential data breach now threatens the organization.
An unspoken truth often emerges from user experiences. Excessively rigid IT policies sometimes fuel Shadow IT adoption. Slow internal procurement processes for new tools can also push users toward unsanctioned alternatives. They find their own solutions. These solutions are often less secure. IT departments must understand user workflow needs. Simply blocking tools without offering viable, efficient alternatives often proves counterproductive. Can a balance truly be struck?
The Ripple Effect: When Shadow IT Fragments Team Collaboration and Data Flow
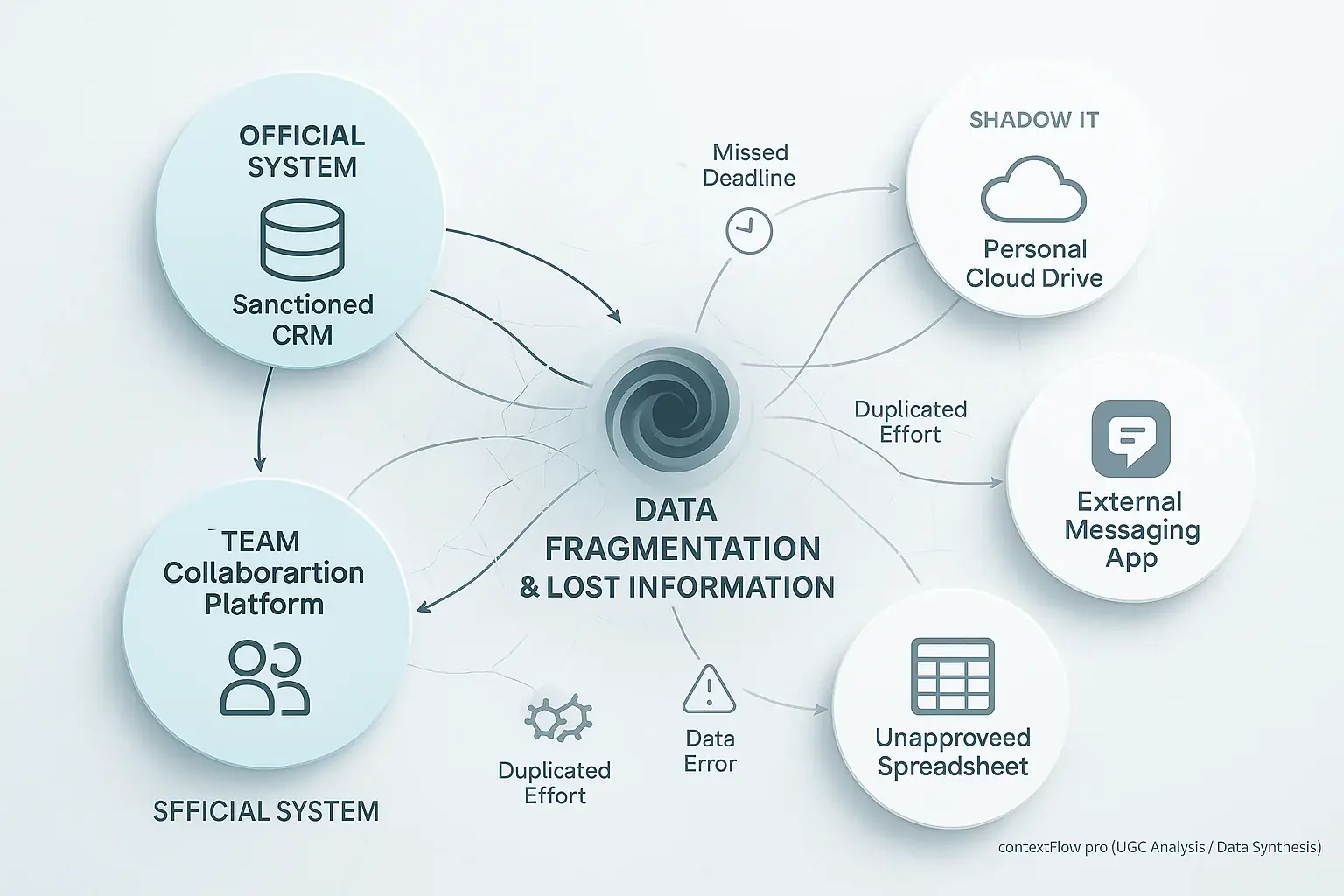
Shadow IT offers individual fixes. Team chaos frequently follows. A team member's unapproved tool creates ripples across workflows. Information becomes siloed. Discussions scatter across fragmented channels. Suddenly, the latest document version is lost. Picture this scenario: Team A uses official, sanctioned chat. Team B simultaneously uses a personal messaging app for its projects. Critical updates get missed. This directly leads to duplicated efforts. Missed deadlines become common. Our analysis of user experiences highlights this recurring breakdown in team synchronization.
Data integrity becomes a substantial headache. Information entered into an unapproved application rarely syncs with central systems. Official records then reflect outdated or incomplete information. This disparity causes glaring discrepancies. Errors proliferate. Professionals subsequently waste considerable time on manual, painstaking re-entry of data. Such disjointed processes directly fracture vital context flow. Productivity plummets.
The true cost of this digital fragmentation often remains hidden from immediate view. It acts as a silent drain on overall team efficiency. This 'slow leak' of resources and focus continues unnoticed by many. Then, a major project derails spectacularly. Or critical, irreplaceable information disappears completely. Collaboration suffers deeply when individuals operate in these isolated digital silos. Team cohesion frays. User narratives consistently reveal this painful, delayed realization of accumulated damage.
Beyond the Bypass: What Shadow IT Really Tells Us About Unmet User Needs

Smart organizations view Shadow IT through a new lens. It is a powerful diagnostic tool. This user behavior clearly signals unmet needs. Official tools are not addressing these needs effectively. Users actively solve genuine problems. Their choice of unapproved applications directly reveals specific pain points within the existing digital infrastructure.
User actions often represent grassroots innovation. They are frequently ahead of the curve. Employees discover more efficient methods. They test new technologies IT might not yet recognize. This is not simple rebellion. It is ingenuity. Imagine a team. They start using a new owner process summarizer for meeting notes. The company's official tool proves too slow. This choice highlights a pressing need for better meeting efficiency. It is far more than a mere security breach.
IT departments find a significant opportunity here. Understanding why users turn to Shadow IT provides crucial intelligence. This insight helps proactively identify tool gaps. It informs improvements to current systems. It can even spotlight new, user-endorsed solutions for wider adoption. This approach builds bridges. It fosters productive collaboration between users and IT, not just constructing higher walls.
Bridging the Gap: Towards a User-Centric Approach to Hybrid Tooling
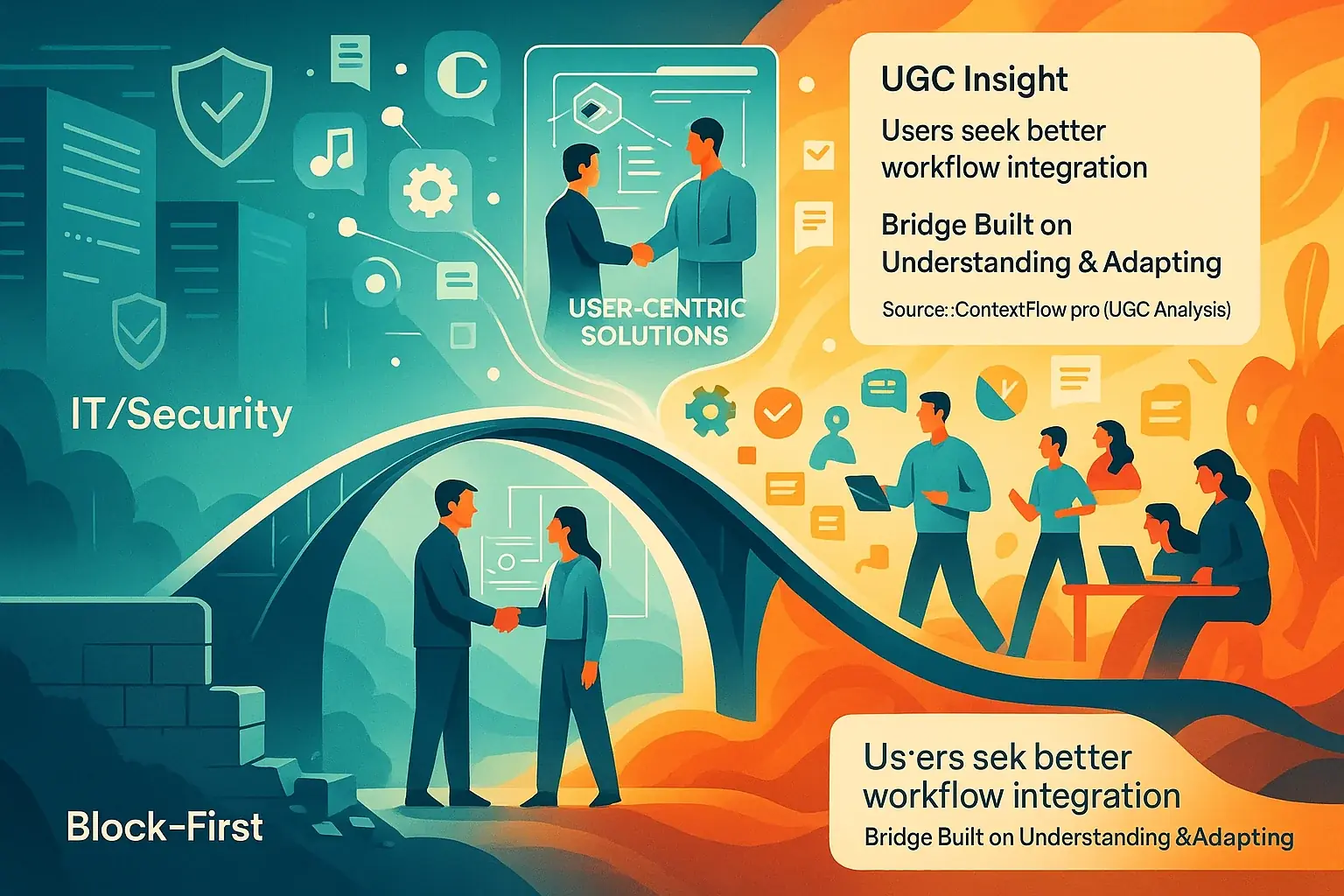
Shadow IT transmits a clear signal. It highlights unmet user needs. Directly. Our UGC analysis shows users bypass approved tools for practical reasons. They seek better workflow integration. Understanding these whys is foundational. This insight unlocks a smoother hybrid environment. It strengthens security. The objective? Understand and adapt. Not just block. This pivotal shift transforms team dynamics.
Organizations must shift perspective. Now. The old 'block-first' mentality fails hybrid teams. A new approach: 'understand-and-adapt'. This path delivers. Involve users. Actively. In tool selection. Prioritize genuine usability. Ensure official tools truly support dynamic hybrid work. What follows? Trust grows. The appeal of rogue solutions fades. IT and users then build bridges, not walls, fostering essential collaboration for genuinely optimized tooling.